---
title: Tanzu Application Platform 1.5 (Full Profile) をKind on OrbStackにインストールするメモ
tags: ["Kubernetes", "Cartographer", "kind", "Tanzu", "TAP"]
categories: ["Dev", "CaaS", "Kubernetes", "TAP"]
date: 2023-07-03T08:17:17Z
updated: 2023-07-10T05:38:46Z
---
[こちらの記事](/entries/746)でOrbStackの紹介を行いましたが、OrbStackを使うとMetalLB on Macが利用可能になるので、
Mac上でさまざまな検証が可能になります。
今回はKind上にHarborとTanzu Application Platformをデプロイしてみます。
Docker Desktopではtype=LoadBalancerなServiceのExternal IP対して、Macから到達できなかったので、
Harborを立ててもMacとTAPのどちらからもアクセスすると言うことができませんでした。
OrbStackならこれが可能になるので、Harborを使ったTAPのインストールをMac上で行えるようになりました。
せっかくなのでFull Profileでインストールしてみます。
**目次**
### kindクラスタの作成
```
kind create cluster --image kindest/node:v1.26.6
```
### Metal LBのインストール
MetalLBインストール
```
kubectl apply -f https://raw.githubusercontent.com/metallb/metallb/v0.13.10/config/manifests/metallb-native.yaml
kubectl wait --namespace metallb-system \
--for=condition=ready pod \
--selector=app=metallb \
--timeout=90s
```
MetalLBが払い出すIP Range(`172.19.255.200-172.19.255.250`)の指定
```
kubectl apply -f https://kind.sigs.k8s.io/examples/loadbalancer/metallb-config.yaml
```
> 次のコマンドの結果が`172.19.0.0/16`でない場合は、metallb-config.yamlを修正する必要があります。
>
> ```
> docker network inspect -f '{{.IPAM.Config}}' kind
> ```
以降、type=LoadBalancerのサービスのExternal IPに`172.19.255.200-172.19.255.250`が利用可能です。
今後の作業で、次のIPを利用します。
* 172.19.255.200 ... TAPのEnvoy
* 172.19.255.210 ... HarborのNginx
### Harborのインストール
Helm ChartでHarborをインストールします。
```
helm repo add harbor https://helm.goharbor.io
helm repo update
```
`helm install`でHarborをインストールします。
```
helm install -n harbor harbor harbor/harbor \
--set expose.type=loadBalancer \
--set expose.tls.auto.commonName=harbor.172-19-255-210.sslip.io \
--set expose.loadBalancer.IP=172.19.255.210 \
--set externalURL=https://harbor.172-19-255-210.sslip.io \
--set persistence.persistentVolumeClaim.registry.size=100Gi \
--create-namespace \
--wait
```
指定したIPでHarborのServiceが作成されていることを確認します。
```
$ kubectl get svc -n harbor harbor
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
harbor LoadBalancer 10.96.193.191 172.19.255.210 80:31838/TCP,443:31811/TCP,4443:30793/TCP 7m
```
https://harbor.172-19-255-210.sslip.io にアクセス。ユーザー名は`admin`、パスワードは`Harbor12345`でログインできます。
 HaborのCA証明書をダウンロードして、Macに信頼させます。
```
kubectl get secret -n harbor harbor-nginx -otemplate='{{index .data "ca.crt" | base64decode}}' > harbor.ca
sudo security add-trusted-cert -d -r trustRoot -k ~/Library/Keychains/login.keychain harbor.ca
```
OrbStackを再起動し、kindのコンテナも起動します。
```
$ kubectl get pod -A
NAMESPACE NAME READY STATUS RESTARTS AGE
harbor harbor-core-549687b886-qzs8p 1/1 Running 1 (76s ago) 25m
harbor harbor-database-0 1/1 Running 1 (76s ago) 25m
harbor harbor-jobservice-576bfc6dff-rhmhm 1/1 Running 4 (52s ago) 25m
harbor harbor-nginx-5d694c7d99-877rv 1/1 Running 2 (57s ago) 25m
harbor harbor-notary-server-64b8d79c8d-qt45q 1/1 Running 1 (76s ago) 25m
harbor harbor-notary-signer-ffcb6d46-s45fq 1/1 Running 1 (76s ago) 25m
harbor harbor-portal-b5cf6864-tgm89 1/1 Running 1 (76s ago) 25m
harbor harbor-redis-0 1/1 Running 1 (76s ago) 25m
harbor harbor-registry-76ff59b67c-mhlkg 2/2 Running 2 (76s ago) 25m
harbor harbor-trivy-0 1/1 Running 1 (76s ago) 25m
kube-system coredns-787d4945fb-98h2g 1/1 Running 2 (76s ago) 77m
kube-system coredns-787d4945fb-vf456 1/1 Running 2 (76s ago) 77m
kube-system etcd-kind-control-plane 1/1 Running 2 (76s ago) 78m
kube-system kindnet-hz8ft 1/1 Running 2 (76s ago) 77m
kube-system kube-apiserver-kind-control-plane 1/1 Running 2 (76s ago) 78m
kube-system kube-controller-manager-kind-control-plane 1/1 Running 2 (76s ago) 78m
kube-system kube-proxy-gtsmt 1/1 Running 2 (76s ago) 77m
kube-system kube-scheduler-kind-control-plane 1/1 Running 2 (76s ago) 78m
local-path-storage local-path-provisioner-6bd6454576-rrwpc 1/1 Running 3 (31s ago) 77m
metallb-system controller-5fd797fbf7-27w6t 1/1 Running 4 (33s ago) 77m
metallb-system speaker-9f5jz 1/1 Running 4 (33s ago) 77m
```
HarborにDockerログインできることを確認します。
```
$ docker login harbor.172-19-255-210.sslip.io -u admin -p Harbor12345
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
Login Succeeded
```
KindのContainerdにHarborのCA証明書を信頼させます。
```
docker exec kind-control-plane mkdir -p /etc/containerd/certs.d
docker cp harbor.ca kind-control-plane:/etc/containerd/certs.d/
cat <
```
#### EULAの承諾
初めてインストールする場合は、以下のコンポーネントのEULAをAcceptしてください。
* [Tanzu Application Platform](https://network.tanzu.vmware.com/products/tanzu-application-platform/)
* [Cluster Essentials for VMware Tanzu](https://network.tanzu.vmware.com/products/tanzu-cluster-essentials/)
> ⚠️ EULAで定められている使用期間は30日間です。とは言え、特にソフトウェア的に制限がかけられているわけではありません。
#### Tanzu CLIのインストール
```
# For Mac
pivnet download-product-files --product-slug='tanzu-application-platform' --release-version='1.5.2' --glob='tanzu-framework-darwin-amd64-*.tar'
# For Linux
pivnet download-product-files --product-slug='tanzu-application-platform' --release-version='1.5.2' --glob='tanzu-framework-linux-amd64-*.tar'
# For Windows
pivnet download-product-files --product-slug='tanzu-application-platform' --release-version='1.5.2' --glob='tanzu-framework-windows-amd64-*.zip'
```
```
tar xvf tanzu-framework-*-amd64-*.tar
install cli/core/v0.28.1/tanzu-core-*_amd64 /usr/local/bin/tanzu
export TANZU_CLI_NO_INIT=true
```
```
$ tanzu version
version: v0.28.1
buildDate: 2023-03-07
sha: 0e6704777-dirty
```
プラグインのインストール
```
tanzu plugin clean
tanzu plugin install --local cli all
```
#### TAP用のHarbor ProjectとRobot Accountsのセットアップ
TAP用のコンテナイメージをRelocationするためにHarborのプロジェクトを作成します。
```
curl -k -u admin:Harbor12345 https://harbor.172-19-255-210.sslip.io/api/v2.0/projects -H "Content-Type: application/json" -d '{"project_name": "tanzu-cluster-essentials", "public": false}'
curl -k -u admin:Harbor12345 https://harbor.172-19-255-210.sslip.io/api/v2.0/projects -H "Content-Type: application/json" -d '{"project_name": "tanzu-application-platform", "public": false}'
```
TAPで使用するHarborのRobot Accountを作成します。
```
mkdir -p robots
curl -s -k -u admin:Harbor12345 https://harbor.172-19-255-210.sslip.io/api/v2.0/robots -H 'Content-Type: application/json' -d '{"duration":-1,"level":"project","name":"tap-rw","permissions":[{"access":[{"action":"pull","resource":"repository"},{"action":"push","resource":"repository"}],"kind":"project","namespace":"tanzu-cluster-essentials"}]}' > robots/tanzu-cluster-essentials-rw.json
curl -s -k -u admin:Harbor12345 https://harbor.172-19-255-210.sslip.io/api/v2.0/robots -H 'Content-Type: application/json' -d '{"duration":-1,"level":"project","name":"tap-ro","permissions":[{"access":[{"action":"pull","resource":"repository"}],"kind":"project","namespace":"tanzu-cluster-essentials"}]}' > robots/tanzu-cluster-essentials-ro.json
curl -s -k -u admin:Harbor12345 https://harbor.172-19-255-210.sslip.io/api/v2.0/robots -H 'Content-Type: application/json' -d '{"duration":-1,"level":"project","name":"tap-rw","permissions":[{"access":[{"action":"pull","resource":"repository"},{"action":"push","resource":"repository"}],"kind":"project","namespace":"tanzu-application-platform"}]}' > robots/tanzu-application-platform-rw.json
```
#### Cluster Essentials for VMware Tanzuのインストール
TAPのインストールに必要なKapp ControllerとSecretgen Controllerをデプロイするために [Cluster Essentials for VMware Tanzu](https://network.tanzu.vmware.com/products/tanzu-cluster-essentials) をインストールします。
```
# Mac
pivnet download-product-files --product-slug='tanzu-cluster-essentials' --release-version='1.5.2' --glob='tanzu-cluster-essentials-darwin-amd64-*'
# Linux
pivnet download-product-files --product-slug='tanzu-cluster-essentials' --release-version='1.5.2' --glob='tanzu-cluster-essentials-linux-amd64-*'
```
Cluster EssentialsをHarborにRelocationします。
```
TANZUNET_USERNAME=...
TANZUNET_PASSWORD=...
export IMGPKG_REGISTRY_HOSTNAME_0=registry.tanzu.vmware.com
export IMGPKG_REGISTRY_USERNAME_0=${TANZUNET_USERNAME}
export IMGPKG_REGISTRY_PASSWORD_0=${TANZUNET_PASSWORD}
export IMGPKG_REGISTRY_HOSTNAME_1=harbor.172-19-255-210.sslip.io
export IMGPKG_REGISTRY_USERNAME_1=$(cat robots/tanzu-cluster-essentials-rw.json | jq -r .name)
export IMGPKG_REGISTRY_PASSWORD_1=$(cat robots/tanzu-cluster-essentials-rw.json | jq -r .secret)
imgpkg copy -b registry.tanzu.vmware.com/tanzu-cluster-essentials/cluster-essentials-bundle:1.5.1 --to-repo harbor.172-19-255-210.sslip.io/tanzu-cluster-essentials/cluster-essentials-bundle
```
Cluster Essentialsをインストールします。
```yaml
mkdir tanzu-cluster-essentials
tar xzvf tanzu-cluster-essentials-*-amd64-*.tgz -C tanzu-cluster-essentials
export INSTALL_BUNDLE=harbor.172-19-255-210.sslip.io/tanzu-cluster-essentials/cluster-essentials-bundle:1.5.1
export INSTALL_REGISTRY_HOSTNAME=harbor.172-19-255-210.sslip.io
export INSTALL_REGISTRY_USERNAME=$(cat robots/tanzu-cluster-essentials-ro.json | jq -r .name)
export INSTALL_REGISTRY_PASSWORD=$(cat robots/tanzu-cluster-essentials-ro.json | jq -r .secret)
export YTT_kappController__config__caCerts=$(cat harbor.ca)
cd tanzu-cluster-essentials
./install.sh --yes
cd ..
```
Podを確認します。
```
$ kubectl get pod -n kapp-controller
NAME READY STATUS RESTARTS AGE
kapp-controller-8557d45b9b-qjbsj 2/2 Running 0 37s
$ kubectl get pod -n secretgen-controller
NAME READY STATUS RESTARTS AGE
secretgen-controller-6b6bf7bb4-ngln4 1/1 Running 0 37s
```
#### TAPのイメージRelocationおよびPackage Repositoryの設定
TAPのイメージをHarborへRelocationします。
```
export IMGPKG_REGISTRY_HOSTNAME_0=registry.tanzu.vmware.com
export IMGPKG_REGISTRY_USERNAME_0=${TANZUNET_USERNAME}
export IMGPKG_REGISTRY_PASSWORD_0=${TANZUNET_PASSWORD}
export IMGPKG_REGISTRY_HOSTNAME_1=harbor.172-19-255-210.sslip.io
export IMGPKG_REGISTRY_USERNAME_1=$(cat robots/tanzu-application-platform-rw.json | jq -r .name)
export IMGPKG_REGISTRY_PASSWORD_1=$(cat robots/tanzu-application-platform-rw.json | jq -r .secret)
imgpkg copy -b registry.tanzu.vmware.com/tanzu-application-platform/tap-packages:1.5.2 --to-repo harbor.172-19-255-210.sslip.io/tanzu-application-platform/tap-packages
imgpkg copy -b registry.tanzu.vmware.com/tanzu-application-platform/full-tbs-deps-package-repo:1.10.10 --to-repo harbor.172-19-255-210.sslip.io/tanzu-application-platform/full-tbs-deps-package-repo
```
TAPのPackage Repositoryを作成します。
```
kubectl create ns tap-install
tanzu secret registry add tap-registry \
--username $(cat robots/tanzu-application-platform-rw.json | jq -r .name) \
--password $(cat robots/tanzu-application-platform-rw.json | jq -r .secret) \
--server harbor.172-19-255-210.sslip.io \
--export-to-all-namespaces \
--yes \
--namespace tap-install
tanzu package repository add tanzu-tap-repository \
--url harbor.172-19-255-210.sslip.io/tanzu-application-platform/tap-packages:1.5.2 \
--namespace tap-install
tanzu package repository add tbs-full-deps-repository \
--url harbor.172-19-255-210.sslip.io/tanzu-application-platform/full-tbs-deps-package-repo:1.10.10 \
--namespace tap-install
```
利用可能なPackage一覧を確認します。
```
$ kubectl get package -n tap-install
NAME PACKAGEMETADATA NAME VERSION AGE
accelerator.apps.tanzu.vmware.com.1.5.3 accelerator.apps.tanzu.vmware.com 1.5.3 21s
api-portal.tanzu.vmware.com.1.3.6 api-portal.tanzu.vmware.com 1.3.6 21s
apis.apps.tanzu.vmware.com.0.3.1 apis.apps.tanzu.vmware.com 0.3.1 21s
apiserver.appliveview.tanzu.vmware.com.1.5.3 apiserver.appliveview.tanzu.vmware.com 1.5.3 21s
app-scanning.apps.tanzu.vmware.com.0.0.1-alpha.4 app-scanning.apps.tanzu.vmware.com 0.0.1-alpha.4 21s
application-configuration-service.tanzu.vmware.com.2.0.6 application-configuration-service.tanzu.vmware.com 2.0.6 21s
backend.appliveview.tanzu.vmware.com.1.5.3 backend.appliveview.tanzu.vmware.com 1.5.3 21s
bitnami.services.tanzu.vmware.com.0.1.0 bitnami.services.tanzu.vmware.com 0.1.0 21s
buildservice.tanzu.vmware.com.1.10.10 buildservice.tanzu.vmware.com 1.10.10 21s
carbonblack.scanning.apps.tanzu.vmware.com.1.2.0-beta.2 carbonblack.scanning.apps.tanzu.vmware.com 1.2.0-beta.2 20s
cartographer.tanzu.vmware.com.0.7.3 cartographer.tanzu.vmware.com 0.7.3 21s
cert-manager.tanzu.vmware.com.2.3.1 cert-manager.tanzu.vmware.com 2.3.1 21s
cnrs.tanzu.vmware.com.2.2.0 cnrs.tanzu.vmware.com 2.2.0 21s
connector.appliveview.tanzu.vmware.com.1.5.3 connector.appliveview.tanzu.vmware.com 1.5.3 21s
contour.tanzu.vmware.com.1.22.5+tap.1.5.0 contour.tanzu.vmware.com 1.22.5+tap.1.5.0 21s
controller.source.apps.tanzu.vmware.com.0.7.1 controller.source.apps.tanzu.vmware.com 0.7.1 21s
conventions.appliveview.tanzu.vmware.com.1.5.3 conventions.appliveview.tanzu.vmware.com 1.5.3 21s
crossplane.tanzu.vmware.com.0.1.1 crossplane.tanzu.vmware.com 0.1.1 21s
developer-conventions.tanzu.vmware.com.0.10.0 developer-conventions.tanzu.vmware.com 0.10.0 21s
eventing.tanzu.vmware.com.2.2.2 eventing.tanzu.vmware.com 2.2.2 21s
external-secrets.apps.tanzu.vmware.com.0.6.1+tap.6 external-secrets.apps.tanzu.vmware.com 0.6.1+tap.6 21s
fluxcd.source.controller.tanzu.vmware.com.0.27.0+tap.10 fluxcd.source.controller.tanzu.vmware.com 0.27.0+tap.10 21s
full-tbs-deps.tanzu.vmware.com.1.10.10 full-tbs-deps.tanzu.vmware.com 1.10.10 15s
grype.scanning.apps.tanzu.vmware.com.1.5.40 grype.scanning.apps.tanzu.vmware.com 1.5.40 21s
learningcenter.tanzu.vmware.com.0.2.7 learningcenter.tanzu.vmware.com 0.2.7 21s
metadata-store.apps.tanzu.vmware.com.1.5.1 metadata-store.apps.tanzu.vmware.com 1.5.1 21s
namespace-provisioner.apps.tanzu.vmware.com.0.3.1 namespace-provisioner.apps.tanzu.vmware.com 0.3.1 21s
ootb-delivery-basic.tanzu.vmware.com.0.12.6 ootb-delivery-basic.tanzu.vmware.com 0.12.6 21s
ootb-supply-chain-basic.tanzu.vmware.com.0.12.6 ootb-supply-chain-basic.tanzu.vmware.com 0.12.6 21s
ootb-supply-chain-testing-scanning.tanzu.vmware.com.0.12.6 ootb-supply-chain-testing-scanning.tanzu.vmware.com 0.12.6 21s
ootb-supply-chain-testing.tanzu.vmware.com.0.12.6 ootb-supply-chain-testing.tanzu.vmware.com 0.12.6 21s
ootb-templates.tanzu.vmware.com.0.12.6 ootb-templates.tanzu.vmware.com 0.12.6 21s
policy.apps.tanzu.vmware.com.1.4.0 policy.apps.tanzu.vmware.com 1.4.0 21s
scanning.apps.tanzu.vmware.com.1.5.42 scanning.apps.tanzu.vmware.com 1.5.42 21s
service-bindings.labs.vmware.com.0.9.1 service-bindings.labs.vmware.com 0.9.1 21s
services-toolkit.tanzu.vmware.com.0.10.2 services-toolkit.tanzu.vmware.com 0.10.2 21s
snyk.scanning.apps.tanzu.vmware.com.1.0.0-beta.43 snyk.scanning.apps.tanzu.vmware.com 1.0.0-beta.43 21s
spring-boot-conventions.tanzu.vmware.com.1.5.3 spring-boot-conventions.tanzu.vmware.com 1.5.3 21s
spring-cloud-gateway.tanzu.vmware.com.2.0.3 spring-cloud-gateway.tanzu.vmware.com 2.0.3 21s
sso.apps.tanzu.vmware.com.3.1.2 sso.apps.tanzu.vmware.com 3.1.2 21s
tap-auth.tanzu.vmware.com.1.1.0 tap-auth.tanzu.vmware.com 1.1.0 21s
tap-gui.tanzu.vmware.com.1.5.3 tap-gui.tanzu.vmware.com 1.5.3 21s
tap-telemetry.tanzu.vmware.com.0.5.1 tap-telemetry.tanzu.vmware.com 0.5.1 21s
tap.tanzu.vmware.com.1.5.2 tap.tanzu.vmware.com 1.5.2 21s
tekton.tanzu.vmware.com.0.41.0+tap.8 tekton.tanzu.vmware.com 0.41.0+tap.8 21s
workshops.learningcenter.tanzu.vmware.com.0.2.6 workshops.learningcenter.tanzu.vmware.com 0.2.6 21s
```
#### Full profileのインストール
https://docs.vmware.com/en/VMware-Tanzu-Application-Platform/1.5/tap/install-online-profile.html
Full Profileをインストールします。
Builderの作成などに使用するBuildservice用のSecretを作成します。
```
tanzu secret registry add buildservice-regcred \
--username $(cat robots/tanzu-application-platform-rw.json | jq -r .name) \
--password $(cat robots/tanzu-application-platform-rw.json | jq -r .secret) \
--server harbor.172-19-255-210.sslip.io \
--yes \
--namespace tap-install
```
`tap-values.yaml`を用意します。せっかくFull profileをインストールするので、Supply Chainは`testing_scanning`にします。また、Buildservice用のdependenciesはfullを使用します。
```yaml
cat < tap-values.yaml
shared:
ingress_domain: tap.172-19-255-200.sslip.io
ingress_issuer: tap-ingress-selfsigned
image_registry:
project_path: harbor.172-19-255-210.sslip.io/tanzu-application-platform
secret:
name: buildservice-regcred
namespace: tap-install
kubernetes_version: "1.26"
ca_cert_data: |
$(cat harbor.ca | sed 's/^/ /g' )
ceip_policy_disclosed: true
profile: full
supply_chain: testing_scanning
contour:
contour:
replicas: 1
envoy:
service:
type: LoadBalancer
loadBalancerIP: 172.19.255.200
buildservice:
exclude_dependencies: true
tap_gui:
metadataStoreAutoconfiguration: true
metadata_store:
ns_for_export_app_cert: "*"
app_service_type: ClusterIP
pg_req_cpu: "200m"
pg_req_memory: "200Mi"
scanning:
metadataStore:
url: "" # Configuration is moved, so set this string to empty.
# 以下リソース節約用
cnrs:
lite:
enable: true
pdb:
enable: false
cartographer:
cartographer:
resources:
requests:
cpu: 100m
memory: 200Mi
crossplane:
resourcesCrossplane:
requests:
cpu: 100m
memory: 200Mi
resourcesRBACManager:
requests:
cpu: 100m
memory: 200Mi
excluded_packages:
- policy.apps.tanzu.vmware.com
- image-policy-webhook.signing.apps.tanzu.vmware.com
- eventing.tanzu.vmware.com
- sso.apps.tanzu.vmware.com
- learningcenter.tanzu.vmware.com
- workshops.learningcenter.tanzu.vmware.com
- api-portal.tanzu.vmware.com
EOF
```
TAPおよびbuildserviceのfull dependenciesをインストールします。
```
tanzu package install tap \
-p tap.tanzu.vmware.com \
-v 1.5.2 \
--values-file tap-values.yaml \
-n tap-install
tanzu package install full-tbs-deps \
-p full-tbs-deps.tanzu.vmware.com \
-v 1.10.10 \
-n tap-install
```
インストールされたAppを確認します。
```
$ kubectl get app -n tap-install
NAME DESCRIPTION SINCE-DEPLOY AGE
accelerator Reconcile succeeded 5m38s 16m
api-auto-registration Reconcile succeeded 7m17s 17m
appliveview Reconcile succeeded 6m24s 16m
appliveview-apiserver Reconcile succeeded 7m5s 17m
appliveview-connector Reconcile succeeded 3m51s 18m
appliveview-conventions Reconcile succeeded 7m7s 17m
bitnami-services Reconcile succeeded 6m57s 17m
buildservice Reconcile succeeded 3m36s 18m
cartographer Reconcile succeeded 7m16s 17m
cert-manager Reconcile succeeded 7m33s 18m
cnrs Reconcile succeeded 6m 16m
contour Reconcile succeeded 6m51s 17m
crossplane Reconcile succeeded 7m55s 18m
developer-conventions Reconcile succeeded 7m 17m
fluxcd-source-controller Reconcile succeeded 7m47s 18m
full-tbs-deps Reconcile succeeded 2m46s 2m46s
grype Reconcile succeeded 6m32s 16m
metadata-store Reconcile succeeded 6m32s 16m
namespace-provisioner Reconcile succeeded 6m32s 18m
ootb-delivery-basic Reconcile succeeded 7m4s 17m
ootb-supply-chain-testing-scanning Reconcile succeeded 7m5s 17m
ootb-templates Reconcile succeeded 7m11s 17m
scanning Reconcile succeeded 3m48s 18m
service-bindings Reconcile succeeded 3m49s 18m
services-toolkit Reconcile succeeded 7m2s 17m
source-controller Reconcile succeeded 7m18s 17m
spring-boot-conventions Reconcile succeeded 7m5s 17m
tap Reconcile succeeded 6m33s 18m
tap-auth Reconcile succeeded 8m6s 18m
tap-gui Reconcile succeeded 6m15s 16m
tap-telemetry Reconcile succeeded 7m59s 18m
tekton-pipelines Reconcile succeeded 3m49s 18m
```
デプロイされたPodは次の通りです。
```
$ kubectl get pod -A | grep -v kube-system | grep -v local-path-storage | grep -v harbor
NAMESPACE NAME READY STATUS RESTARTS AGE
accelerator-system acc-engine-749f549c9d-h9b99 1/1 Running 0 11m
accelerator-system acc-server-fc7dd79b6-wvmfg 1/1 Running 0 11m
accelerator-system accelerator-controller-manager-75d49d6b6d-pxqmq 1/1 Running 0 11m
api-auto-registration api-auto-registration-controller-865dc6866d-tm5gc 1/1 Running 0 12m
app-live-view-connector application-live-view-connector-h96fx 1/1 Running 0 12m
app-live-view-conventions appliveview-webhook-5546c9dd85-62xsv 1/1 Running 0 11m
app-live-view application-live-view-server-645f777f78-gdbvg 1/1 Running 0 11m
appliveview-tokens-system appliveview-apiserver-59669dbf86-8sk89 1/1 Running 0 12m
build-service build-pod-image-fetcher-zzchl 5/5 Running 0 12m
build-service dependency-updater-controller-67996966c4-58cx4 1/1 Running 0 12m
build-service secret-syncer-controller-654f46847-zrmch 1/1 Running 0 12m
build-service warmer-controller-665bf84b55-d5zz4 1/1 Running 0 12m
cartographer-system cartographer-controller-b49896f86-gklpw 1/1 Running 0 12m
cartographer-system cartographer-conventions-controller-manager-6759cf6cdb-csx77 1/1 Running 0 12m
cert-injection-webhook cert-injection-webhook-6dbbcb6744-24xdv 1/1 Running 0 12m
cert-manager cert-manager-6cfb79886-q77nm 1/1 Running 0 12m
cert-manager cert-manager-cainjector-6dc5d6dd7c-dvpf7 1/1 Running 0 12m
cert-manager cert-manager-webhook-697d9df55f-982q2 1/1 Running 0 12m
crossplane-system crossplane-96c5dc974-l8ccm 1/1 Running 0 12m
crossplane-system crossplane-rbac-manager-6d5c4846bf-bp89p 1/1 Running 0 12m
developer-conventions webhook-5bd857bff9-vsb5f 1/1 Running 0 11m
flux-system fluxcd-source-controller-69775f9d86-2ghzb 1/1 Running 0 12m
kapp-controller kapp-controller-8557d45b9b-qjbsj 2/2 Running 0 92m
knative-serving activator-798dfb4fd9-wkl92 1/1 Running 0 11m
knative-serving autoscaler-f774579c5-kpclb 1/1 Running 0 11m
knative-serving autoscaler-hpa-c69bd89cc-r8kdr 1/1 Running 0 11m
knative-serving controller-69f7c598dc-5llrj 1/1 Running 0 11m
knative-serving domain-mapping-8489f8f965-9zs9q 1/1 Running 0 11m
knative-serving domainmapping-webhook-6748df54f9-8s7mp 1/1 Running 0 11m
knative-serving net-certmanager-controller-85b5b7df47-xhrf4 1/1 Running 0 11m
knative-serving net-certmanager-webhook-576f5b96db-297hw 1/1 Running 0 11m
knative-serving net-contour-controller-57755b65bb-q5wkt 1/1 Running 0 11m
knative-serving webhook-65f8998845-m2z68 1/1 Running 0 11m
kpack kpack-controller-7b8f4744d5-qbrwm 1/1 Running 0 12m
kpack kpack-webhook-bdcb8dfdd-gkv9p 1/1 Running 0 12m
metadata-store metadata-store-app-6969d75d48-fm6k9 2/2 Running 0 11m
metadata-store metadata-store-db-0 1/1 Running 0 67s
metallb-system controller-5fd797fbf7-27w6t 1/1 Running 4 (146m ago) 3h43m
metallb-system speaker-9f5jz 1/1 Running 4 (146m ago) 3h43m
scan-link-system scan-link-controller-manager-86d4cccb6f-qwm8j 2/2 Running 0 13m
secretgen-controller secretgen-controller-6b6bf7bb4-ngln4 1/1 Running 0 92m
service-bindings manager-5b96494bbb-4k7p5 1/1 Running 0 12m
services-toolkit resource-claims-apiserver-77fbfb557b-jtgnl 1/1 Running 0 12m
services-toolkit services-toolkit-controller-manager-7c8dbcbc4c-7bvmt 1/1 Running 0 12m
source-system source-controller-manager-86c85f86d8-kzvt9 1/1 Running 0 12m
spring-boot-convention spring-boot-webhook-78b667b84b-k6d6b 1/1 Running 0 11m
stacks-operator-system controller-manager-fdd95c5cf-9x48t 1/1 Running 0 12m
tanzu-system-ingress contour-cb9f65866-skcdz 1/1 Running 0 12m
tanzu-system-ingress envoy-w4vzd 2/2 Running 0 12m
tap-gui server-6f76d665bd-q4f8v 1/1 Running 0 11m
tap-namespace-provisioning controller-manager-858bf5774d-7ccft 1/1 Running 0 12m
tap-telemetry tap-telemetry-informer-665875499-c2z64 1/1 Running 0 13m
tekton-pipelines-resolvers tekton-pipelines-remote-resolvers-7c488ccc6c-4xmk8 1/1 Running 0 12m
tekton-pipelines tekton-pipelines-controller-76d65c8598-q47jj 1/1 Running 0 12m
tekton-pipelines tekton-pipelines-webhook-d997857cb-858js 1/1 Running 0 12m
```
`tap-values.yaml`に指定したLoadBalancer IPがEnvoyにアサインされていることを確認します。
```
$ kubectl get svc -n tanzu-system-ingress envoy
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
envoy LoadBalancer 10.96.201.188 172.19.255.200 80:31403/TCP,443:31602/TCP 12m
```
インストールされたBuilder一覧を確認します。
```
$ kubectl get clusterbuilder
NAME LATESTIMAGE READY
base harbor.172-19-255-210.sslip.io/tanzu-application-platform/buildservice:clusterbuilder-base@sha256:6bebd5b815488484d2881568869b9e262bfe9512d8343323149625177782d3a9 True
base-jammy harbor.172-19-255-210.sslip.io/tanzu-application-platform/buildservice:clusterbuilder-base-jammy@sha256:109d61c4afc687f464c9c84a8342395c8a9bedec898c0c7a1e88f50021a94b7f True
default harbor.172-19-255-210.sslip.io/tanzu-application-platform/buildservice:clusterbuilder-default@sha256:109d61c4afc687f464c9c84a8342395c8a9bedec898c0c7a1e88f50021a94b7f True
full harbor.172-19-255-210.sslip.io/tanzu-application-platform/buildservice:clusterbuilder-full@sha256:f7ecd1d9298967dd98db51ac3745e22cf8b8a5a1043e8b0e4ac83202b9ceba1b True
full-jammy harbor.172-19-255-210.sslip.io/tanzu-application-platform/buildservice:clusterbuilder-full-jammy@sha256:575cb0da8b74e966e8e115655a37cacf2e3d17605c3fdebea7d5b5cb1c7608cf True
tiny harbor.172-19-255-210.sslip.io/tanzu-application-platform/buildservice:clusterbuilder-tiny@sha256:1b76b0d7a2effd2eba15171df8e4c018936f3f7290a8b2880908abe58c19ffce True
tiny-jammy harbor.172-19-255-210.sslip.io/tanzu-application-platform/buildservice:clusterbuilder-tiny-jammy@sha256:916c6a0111a55e2cd9603dc95818e91ad24b73f785d5e93428adbf1b1872f6f6 True
```
公開されているエンドポイント一覧を確認します。
```
$ kubectl get httpproxy -A
NAMESPACE NAME FQDN TLS SECRET STATUS STATUS DESCRIPTION
metadata-store metadata-store-ingress metadata-store.tap.172-19-255-200.sslip.io ingress-cert valid Valid HTTPProxy
tap-gui tap-gui tap-gui.tap.172-19-255-200.sslip.io tap-gui-cert valid Valid HTTPProxy
```
https://tap-gui.tap.172-19-255-200.sslip.io でTAP GUIにアクセスします。
HaborのCA証明書をダウンロードして、Macに信頼させます。
```
kubectl get secret -n harbor harbor-nginx -otemplate='{{index .data "ca.crt" | base64decode}}' > harbor.ca
sudo security add-trusted-cert -d -r trustRoot -k ~/Library/Keychains/login.keychain harbor.ca
```
OrbStackを再起動し、kindのコンテナも起動します。
```
$ kubectl get pod -A
NAMESPACE NAME READY STATUS RESTARTS AGE
harbor harbor-core-549687b886-qzs8p 1/1 Running 1 (76s ago) 25m
harbor harbor-database-0 1/1 Running 1 (76s ago) 25m
harbor harbor-jobservice-576bfc6dff-rhmhm 1/1 Running 4 (52s ago) 25m
harbor harbor-nginx-5d694c7d99-877rv 1/1 Running 2 (57s ago) 25m
harbor harbor-notary-server-64b8d79c8d-qt45q 1/1 Running 1 (76s ago) 25m
harbor harbor-notary-signer-ffcb6d46-s45fq 1/1 Running 1 (76s ago) 25m
harbor harbor-portal-b5cf6864-tgm89 1/1 Running 1 (76s ago) 25m
harbor harbor-redis-0 1/1 Running 1 (76s ago) 25m
harbor harbor-registry-76ff59b67c-mhlkg 2/2 Running 2 (76s ago) 25m
harbor harbor-trivy-0 1/1 Running 1 (76s ago) 25m
kube-system coredns-787d4945fb-98h2g 1/1 Running 2 (76s ago) 77m
kube-system coredns-787d4945fb-vf456 1/1 Running 2 (76s ago) 77m
kube-system etcd-kind-control-plane 1/1 Running 2 (76s ago) 78m
kube-system kindnet-hz8ft 1/1 Running 2 (76s ago) 77m
kube-system kube-apiserver-kind-control-plane 1/1 Running 2 (76s ago) 78m
kube-system kube-controller-manager-kind-control-plane 1/1 Running 2 (76s ago) 78m
kube-system kube-proxy-gtsmt 1/1 Running 2 (76s ago) 77m
kube-system kube-scheduler-kind-control-plane 1/1 Running 2 (76s ago) 78m
local-path-storage local-path-provisioner-6bd6454576-rrwpc 1/1 Running 3 (31s ago) 77m
metallb-system controller-5fd797fbf7-27w6t 1/1 Running 4 (33s ago) 77m
metallb-system speaker-9f5jz 1/1 Running 4 (33s ago) 77m
```
HarborにDockerログインできることを確認します。
```
$ docker login harbor.172-19-255-210.sslip.io -u admin -p Harbor12345
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
Login Succeeded
```
KindのContainerdにHarborのCA証明書を信頼させます。
```
docker exec kind-control-plane mkdir -p /etc/containerd/certs.d
docker cp harbor.ca kind-control-plane:/etc/containerd/certs.d/
cat <
```
#### EULAの承諾
初めてインストールする場合は、以下のコンポーネントのEULAをAcceptしてください。
* [Tanzu Application Platform](https://network.tanzu.vmware.com/products/tanzu-application-platform/)
* [Cluster Essentials for VMware Tanzu](https://network.tanzu.vmware.com/products/tanzu-cluster-essentials/)
> ⚠️ EULAで定められている使用期間は30日間です。とは言え、特にソフトウェア的に制限がかけられているわけではありません。
#### Tanzu CLIのインストール
```
# For Mac
pivnet download-product-files --product-slug='tanzu-application-platform' --release-version='1.5.2' --glob='tanzu-framework-darwin-amd64-*.tar'
# For Linux
pivnet download-product-files --product-slug='tanzu-application-platform' --release-version='1.5.2' --glob='tanzu-framework-linux-amd64-*.tar'
# For Windows
pivnet download-product-files --product-slug='tanzu-application-platform' --release-version='1.5.2' --glob='tanzu-framework-windows-amd64-*.zip'
```
```
tar xvf tanzu-framework-*-amd64-*.tar
install cli/core/v0.28.1/tanzu-core-*_amd64 /usr/local/bin/tanzu
export TANZU_CLI_NO_INIT=true
```
```
$ tanzu version
version: v0.28.1
buildDate: 2023-03-07
sha: 0e6704777-dirty
```
プラグインのインストール
```
tanzu plugin clean
tanzu plugin install --local cli all
```
#### TAP用のHarbor ProjectとRobot Accountsのセットアップ
TAP用のコンテナイメージをRelocationするためにHarborのプロジェクトを作成します。
```
curl -k -u admin:Harbor12345 https://harbor.172-19-255-210.sslip.io/api/v2.0/projects -H "Content-Type: application/json" -d '{"project_name": "tanzu-cluster-essentials", "public": false}'
curl -k -u admin:Harbor12345 https://harbor.172-19-255-210.sslip.io/api/v2.0/projects -H "Content-Type: application/json" -d '{"project_name": "tanzu-application-platform", "public": false}'
```
TAPで使用するHarborのRobot Accountを作成します。
```
mkdir -p robots
curl -s -k -u admin:Harbor12345 https://harbor.172-19-255-210.sslip.io/api/v2.0/robots -H 'Content-Type: application/json' -d '{"duration":-1,"level":"project","name":"tap-rw","permissions":[{"access":[{"action":"pull","resource":"repository"},{"action":"push","resource":"repository"}],"kind":"project","namespace":"tanzu-cluster-essentials"}]}' > robots/tanzu-cluster-essentials-rw.json
curl -s -k -u admin:Harbor12345 https://harbor.172-19-255-210.sslip.io/api/v2.0/robots -H 'Content-Type: application/json' -d '{"duration":-1,"level":"project","name":"tap-ro","permissions":[{"access":[{"action":"pull","resource":"repository"}],"kind":"project","namespace":"tanzu-cluster-essentials"}]}' > robots/tanzu-cluster-essentials-ro.json
curl -s -k -u admin:Harbor12345 https://harbor.172-19-255-210.sslip.io/api/v2.0/robots -H 'Content-Type: application/json' -d '{"duration":-1,"level":"project","name":"tap-rw","permissions":[{"access":[{"action":"pull","resource":"repository"},{"action":"push","resource":"repository"}],"kind":"project","namespace":"tanzu-application-platform"}]}' > robots/tanzu-application-platform-rw.json
```
#### Cluster Essentials for VMware Tanzuのインストール
TAPのインストールに必要なKapp ControllerとSecretgen Controllerをデプロイするために [Cluster Essentials for VMware Tanzu](https://network.tanzu.vmware.com/products/tanzu-cluster-essentials) をインストールします。
```
# Mac
pivnet download-product-files --product-slug='tanzu-cluster-essentials' --release-version='1.5.2' --glob='tanzu-cluster-essentials-darwin-amd64-*'
# Linux
pivnet download-product-files --product-slug='tanzu-cluster-essentials' --release-version='1.5.2' --glob='tanzu-cluster-essentials-linux-amd64-*'
```
Cluster EssentialsをHarborにRelocationします。
```
TANZUNET_USERNAME=...
TANZUNET_PASSWORD=...
export IMGPKG_REGISTRY_HOSTNAME_0=registry.tanzu.vmware.com
export IMGPKG_REGISTRY_USERNAME_0=${TANZUNET_USERNAME}
export IMGPKG_REGISTRY_PASSWORD_0=${TANZUNET_PASSWORD}
export IMGPKG_REGISTRY_HOSTNAME_1=harbor.172-19-255-210.sslip.io
export IMGPKG_REGISTRY_USERNAME_1=$(cat robots/tanzu-cluster-essentials-rw.json | jq -r .name)
export IMGPKG_REGISTRY_PASSWORD_1=$(cat robots/tanzu-cluster-essentials-rw.json | jq -r .secret)
imgpkg copy -b registry.tanzu.vmware.com/tanzu-cluster-essentials/cluster-essentials-bundle:1.5.1 --to-repo harbor.172-19-255-210.sslip.io/tanzu-cluster-essentials/cluster-essentials-bundle
```
Cluster Essentialsをインストールします。
```yaml
mkdir tanzu-cluster-essentials
tar xzvf tanzu-cluster-essentials-*-amd64-*.tgz -C tanzu-cluster-essentials
export INSTALL_BUNDLE=harbor.172-19-255-210.sslip.io/tanzu-cluster-essentials/cluster-essentials-bundle:1.5.1
export INSTALL_REGISTRY_HOSTNAME=harbor.172-19-255-210.sslip.io
export INSTALL_REGISTRY_USERNAME=$(cat robots/tanzu-cluster-essentials-ro.json | jq -r .name)
export INSTALL_REGISTRY_PASSWORD=$(cat robots/tanzu-cluster-essentials-ro.json | jq -r .secret)
export YTT_kappController__config__caCerts=$(cat harbor.ca)
cd tanzu-cluster-essentials
./install.sh --yes
cd ..
```
Podを確認します。
```
$ kubectl get pod -n kapp-controller
NAME READY STATUS RESTARTS AGE
kapp-controller-8557d45b9b-qjbsj 2/2 Running 0 37s
$ kubectl get pod -n secretgen-controller
NAME READY STATUS RESTARTS AGE
secretgen-controller-6b6bf7bb4-ngln4 1/1 Running 0 37s
```
#### TAPのイメージRelocationおよびPackage Repositoryの設定
TAPのイメージをHarborへRelocationします。
```
export IMGPKG_REGISTRY_HOSTNAME_0=registry.tanzu.vmware.com
export IMGPKG_REGISTRY_USERNAME_0=${TANZUNET_USERNAME}
export IMGPKG_REGISTRY_PASSWORD_0=${TANZUNET_PASSWORD}
export IMGPKG_REGISTRY_HOSTNAME_1=harbor.172-19-255-210.sslip.io
export IMGPKG_REGISTRY_USERNAME_1=$(cat robots/tanzu-application-platform-rw.json | jq -r .name)
export IMGPKG_REGISTRY_PASSWORD_1=$(cat robots/tanzu-application-platform-rw.json | jq -r .secret)
imgpkg copy -b registry.tanzu.vmware.com/tanzu-application-platform/tap-packages:1.5.2 --to-repo harbor.172-19-255-210.sslip.io/tanzu-application-platform/tap-packages
imgpkg copy -b registry.tanzu.vmware.com/tanzu-application-platform/full-tbs-deps-package-repo:1.10.10 --to-repo harbor.172-19-255-210.sslip.io/tanzu-application-platform/full-tbs-deps-package-repo
```
TAPのPackage Repositoryを作成します。
```
kubectl create ns tap-install
tanzu secret registry add tap-registry \
--username $(cat robots/tanzu-application-platform-rw.json | jq -r .name) \
--password $(cat robots/tanzu-application-platform-rw.json | jq -r .secret) \
--server harbor.172-19-255-210.sslip.io \
--export-to-all-namespaces \
--yes \
--namespace tap-install
tanzu package repository add tanzu-tap-repository \
--url harbor.172-19-255-210.sslip.io/tanzu-application-platform/tap-packages:1.5.2 \
--namespace tap-install
tanzu package repository add tbs-full-deps-repository \
--url harbor.172-19-255-210.sslip.io/tanzu-application-platform/full-tbs-deps-package-repo:1.10.10 \
--namespace tap-install
```
利用可能なPackage一覧を確認します。
```
$ kubectl get package -n tap-install
NAME PACKAGEMETADATA NAME VERSION AGE
accelerator.apps.tanzu.vmware.com.1.5.3 accelerator.apps.tanzu.vmware.com 1.5.3 21s
api-portal.tanzu.vmware.com.1.3.6 api-portal.tanzu.vmware.com 1.3.6 21s
apis.apps.tanzu.vmware.com.0.3.1 apis.apps.tanzu.vmware.com 0.3.1 21s
apiserver.appliveview.tanzu.vmware.com.1.5.3 apiserver.appliveview.tanzu.vmware.com 1.5.3 21s
app-scanning.apps.tanzu.vmware.com.0.0.1-alpha.4 app-scanning.apps.tanzu.vmware.com 0.0.1-alpha.4 21s
application-configuration-service.tanzu.vmware.com.2.0.6 application-configuration-service.tanzu.vmware.com 2.0.6 21s
backend.appliveview.tanzu.vmware.com.1.5.3 backend.appliveview.tanzu.vmware.com 1.5.3 21s
bitnami.services.tanzu.vmware.com.0.1.0 bitnami.services.tanzu.vmware.com 0.1.0 21s
buildservice.tanzu.vmware.com.1.10.10 buildservice.tanzu.vmware.com 1.10.10 21s
carbonblack.scanning.apps.tanzu.vmware.com.1.2.0-beta.2 carbonblack.scanning.apps.tanzu.vmware.com 1.2.0-beta.2 20s
cartographer.tanzu.vmware.com.0.7.3 cartographer.tanzu.vmware.com 0.7.3 21s
cert-manager.tanzu.vmware.com.2.3.1 cert-manager.tanzu.vmware.com 2.3.1 21s
cnrs.tanzu.vmware.com.2.2.0 cnrs.tanzu.vmware.com 2.2.0 21s
connector.appliveview.tanzu.vmware.com.1.5.3 connector.appliveview.tanzu.vmware.com 1.5.3 21s
contour.tanzu.vmware.com.1.22.5+tap.1.5.0 contour.tanzu.vmware.com 1.22.5+tap.1.5.0 21s
controller.source.apps.tanzu.vmware.com.0.7.1 controller.source.apps.tanzu.vmware.com 0.7.1 21s
conventions.appliveview.tanzu.vmware.com.1.5.3 conventions.appliveview.tanzu.vmware.com 1.5.3 21s
crossplane.tanzu.vmware.com.0.1.1 crossplane.tanzu.vmware.com 0.1.1 21s
developer-conventions.tanzu.vmware.com.0.10.0 developer-conventions.tanzu.vmware.com 0.10.0 21s
eventing.tanzu.vmware.com.2.2.2 eventing.tanzu.vmware.com 2.2.2 21s
external-secrets.apps.tanzu.vmware.com.0.6.1+tap.6 external-secrets.apps.tanzu.vmware.com 0.6.1+tap.6 21s
fluxcd.source.controller.tanzu.vmware.com.0.27.0+tap.10 fluxcd.source.controller.tanzu.vmware.com 0.27.0+tap.10 21s
full-tbs-deps.tanzu.vmware.com.1.10.10 full-tbs-deps.tanzu.vmware.com 1.10.10 15s
grype.scanning.apps.tanzu.vmware.com.1.5.40 grype.scanning.apps.tanzu.vmware.com 1.5.40 21s
learningcenter.tanzu.vmware.com.0.2.7 learningcenter.tanzu.vmware.com 0.2.7 21s
metadata-store.apps.tanzu.vmware.com.1.5.1 metadata-store.apps.tanzu.vmware.com 1.5.1 21s
namespace-provisioner.apps.tanzu.vmware.com.0.3.1 namespace-provisioner.apps.tanzu.vmware.com 0.3.1 21s
ootb-delivery-basic.tanzu.vmware.com.0.12.6 ootb-delivery-basic.tanzu.vmware.com 0.12.6 21s
ootb-supply-chain-basic.tanzu.vmware.com.0.12.6 ootb-supply-chain-basic.tanzu.vmware.com 0.12.6 21s
ootb-supply-chain-testing-scanning.tanzu.vmware.com.0.12.6 ootb-supply-chain-testing-scanning.tanzu.vmware.com 0.12.6 21s
ootb-supply-chain-testing.tanzu.vmware.com.0.12.6 ootb-supply-chain-testing.tanzu.vmware.com 0.12.6 21s
ootb-templates.tanzu.vmware.com.0.12.6 ootb-templates.tanzu.vmware.com 0.12.6 21s
policy.apps.tanzu.vmware.com.1.4.0 policy.apps.tanzu.vmware.com 1.4.0 21s
scanning.apps.tanzu.vmware.com.1.5.42 scanning.apps.tanzu.vmware.com 1.5.42 21s
service-bindings.labs.vmware.com.0.9.1 service-bindings.labs.vmware.com 0.9.1 21s
services-toolkit.tanzu.vmware.com.0.10.2 services-toolkit.tanzu.vmware.com 0.10.2 21s
snyk.scanning.apps.tanzu.vmware.com.1.0.0-beta.43 snyk.scanning.apps.tanzu.vmware.com 1.0.0-beta.43 21s
spring-boot-conventions.tanzu.vmware.com.1.5.3 spring-boot-conventions.tanzu.vmware.com 1.5.3 21s
spring-cloud-gateway.tanzu.vmware.com.2.0.3 spring-cloud-gateway.tanzu.vmware.com 2.0.3 21s
sso.apps.tanzu.vmware.com.3.1.2 sso.apps.tanzu.vmware.com 3.1.2 21s
tap-auth.tanzu.vmware.com.1.1.0 tap-auth.tanzu.vmware.com 1.1.0 21s
tap-gui.tanzu.vmware.com.1.5.3 tap-gui.tanzu.vmware.com 1.5.3 21s
tap-telemetry.tanzu.vmware.com.0.5.1 tap-telemetry.tanzu.vmware.com 0.5.1 21s
tap.tanzu.vmware.com.1.5.2 tap.tanzu.vmware.com 1.5.2 21s
tekton.tanzu.vmware.com.0.41.0+tap.8 tekton.tanzu.vmware.com 0.41.0+tap.8 21s
workshops.learningcenter.tanzu.vmware.com.0.2.6 workshops.learningcenter.tanzu.vmware.com 0.2.6 21s
```
#### Full profileのインストール
https://docs.vmware.com/en/VMware-Tanzu-Application-Platform/1.5/tap/install-online-profile.html
Full Profileをインストールします。
Builderの作成などに使用するBuildservice用のSecretを作成します。
```
tanzu secret registry add buildservice-regcred \
--username $(cat robots/tanzu-application-platform-rw.json | jq -r .name) \
--password $(cat robots/tanzu-application-platform-rw.json | jq -r .secret) \
--server harbor.172-19-255-210.sslip.io \
--yes \
--namespace tap-install
```
`tap-values.yaml`を用意します。せっかくFull profileをインストールするので、Supply Chainは`testing_scanning`にします。また、Buildservice用のdependenciesはfullを使用します。
```yaml
cat < tap-values.yaml
shared:
ingress_domain: tap.172-19-255-200.sslip.io
ingress_issuer: tap-ingress-selfsigned
image_registry:
project_path: harbor.172-19-255-210.sslip.io/tanzu-application-platform
secret:
name: buildservice-regcred
namespace: tap-install
kubernetes_version: "1.26"
ca_cert_data: |
$(cat harbor.ca | sed 's/^/ /g' )
ceip_policy_disclosed: true
profile: full
supply_chain: testing_scanning
contour:
contour:
replicas: 1
envoy:
service:
type: LoadBalancer
loadBalancerIP: 172.19.255.200
buildservice:
exclude_dependencies: true
tap_gui:
metadataStoreAutoconfiguration: true
metadata_store:
ns_for_export_app_cert: "*"
app_service_type: ClusterIP
pg_req_cpu: "200m"
pg_req_memory: "200Mi"
scanning:
metadataStore:
url: "" # Configuration is moved, so set this string to empty.
# 以下リソース節約用
cnrs:
lite:
enable: true
pdb:
enable: false
cartographer:
cartographer:
resources:
requests:
cpu: 100m
memory: 200Mi
crossplane:
resourcesCrossplane:
requests:
cpu: 100m
memory: 200Mi
resourcesRBACManager:
requests:
cpu: 100m
memory: 200Mi
excluded_packages:
- policy.apps.tanzu.vmware.com
- image-policy-webhook.signing.apps.tanzu.vmware.com
- eventing.tanzu.vmware.com
- sso.apps.tanzu.vmware.com
- learningcenter.tanzu.vmware.com
- workshops.learningcenter.tanzu.vmware.com
- api-portal.tanzu.vmware.com
EOF
```
TAPおよびbuildserviceのfull dependenciesをインストールします。
```
tanzu package install tap \
-p tap.tanzu.vmware.com \
-v 1.5.2 \
--values-file tap-values.yaml \
-n tap-install
tanzu package install full-tbs-deps \
-p full-tbs-deps.tanzu.vmware.com \
-v 1.10.10 \
-n tap-install
```
インストールされたAppを確認します。
```
$ kubectl get app -n tap-install
NAME DESCRIPTION SINCE-DEPLOY AGE
accelerator Reconcile succeeded 5m38s 16m
api-auto-registration Reconcile succeeded 7m17s 17m
appliveview Reconcile succeeded 6m24s 16m
appliveview-apiserver Reconcile succeeded 7m5s 17m
appliveview-connector Reconcile succeeded 3m51s 18m
appliveview-conventions Reconcile succeeded 7m7s 17m
bitnami-services Reconcile succeeded 6m57s 17m
buildservice Reconcile succeeded 3m36s 18m
cartographer Reconcile succeeded 7m16s 17m
cert-manager Reconcile succeeded 7m33s 18m
cnrs Reconcile succeeded 6m 16m
contour Reconcile succeeded 6m51s 17m
crossplane Reconcile succeeded 7m55s 18m
developer-conventions Reconcile succeeded 7m 17m
fluxcd-source-controller Reconcile succeeded 7m47s 18m
full-tbs-deps Reconcile succeeded 2m46s 2m46s
grype Reconcile succeeded 6m32s 16m
metadata-store Reconcile succeeded 6m32s 16m
namespace-provisioner Reconcile succeeded 6m32s 18m
ootb-delivery-basic Reconcile succeeded 7m4s 17m
ootb-supply-chain-testing-scanning Reconcile succeeded 7m5s 17m
ootb-templates Reconcile succeeded 7m11s 17m
scanning Reconcile succeeded 3m48s 18m
service-bindings Reconcile succeeded 3m49s 18m
services-toolkit Reconcile succeeded 7m2s 17m
source-controller Reconcile succeeded 7m18s 17m
spring-boot-conventions Reconcile succeeded 7m5s 17m
tap Reconcile succeeded 6m33s 18m
tap-auth Reconcile succeeded 8m6s 18m
tap-gui Reconcile succeeded 6m15s 16m
tap-telemetry Reconcile succeeded 7m59s 18m
tekton-pipelines Reconcile succeeded 3m49s 18m
```
デプロイされたPodは次の通りです。
```
$ kubectl get pod -A | grep -v kube-system | grep -v local-path-storage | grep -v harbor
NAMESPACE NAME READY STATUS RESTARTS AGE
accelerator-system acc-engine-749f549c9d-h9b99 1/1 Running 0 11m
accelerator-system acc-server-fc7dd79b6-wvmfg 1/1 Running 0 11m
accelerator-system accelerator-controller-manager-75d49d6b6d-pxqmq 1/1 Running 0 11m
api-auto-registration api-auto-registration-controller-865dc6866d-tm5gc 1/1 Running 0 12m
app-live-view-connector application-live-view-connector-h96fx 1/1 Running 0 12m
app-live-view-conventions appliveview-webhook-5546c9dd85-62xsv 1/1 Running 0 11m
app-live-view application-live-view-server-645f777f78-gdbvg 1/1 Running 0 11m
appliveview-tokens-system appliveview-apiserver-59669dbf86-8sk89 1/1 Running 0 12m
build-service build-pod-image-fetcher-zzchl 5/5 Running 0 12m
build-service dependency-updater-controller-67996966c4-58cx4 1/1 Running 0 12m
build-service secret-syncer-controller-654f46847-zrmch 1/1 Running 0 12m
build-service warmer-controller-665bf84b55-d5zz4 1/1 Running 0 12m
cartographer-system cartographer-controller-b49896f86-gklpw 1/1 Running 0 12m
cartographer-system cartographer-conventions-controller-manager-6759cf6cdb-csx77 1/1 Running 0 12m
cert-injection-webhook cert-injection-webhook-6dbbcb6744-24xdv 1/1 Running 0 12m
cert-manager cert-manager-6cfb79886-q77nm 1/1 Running 0 12m
cert-manager cert-manager-cainjector-6dc5d6dd7c-dvpf7 1/1 Running 0 12m
cert-manager cert-manager-webhook-697d9df55f-982q2 1/1 Running 0 12m
crossplane-system crossplane-96c5dc974-l8ccm 1/1 Running 0 12m
crossplane-system crossplane-rbac-manager-6d5c4846bf-bp89p 1/1 Running 0 12m
developer-conventions webhook-5bd857bff9-vsb5f 1/1 Running 0 11m
flux-system fluxcd-source-controller-69775f9d86-2ghzb 1/1 Running 0 12m
kapp-controller kapp-controller-8557d45b9b-qjbsj 2/2 Running 0 92m
knative-serving activator-798dfb4fd9-wkl92 1/1 Running 0 11m
knative-serving autoscaler-f774579c5-kpclb 1/1 Running 0 11m
knative-serving autoscaler-hpa-c69bd89cc-r8kdr 1/1 Running 0 11m
knative-serving controller-69f7c598dc-5llrj 1/1 Running 0 11m
knative-serving domain-mapping-8489f8f965-9zs9q 1/1 Running 0 11m
knative-serving domainmapping-webhook-6748df54f9-8s7mp 1/1 Running 0 11m
knative-serving net-certmanager-controller-85b5b7df47-xhrf4 1/1 Running 0 11m
knative-serving net-certmanager-webhook-576f5b96db-297hw 1/1 Running 0 11m
knative-serving net-contour-controller-57755b65bb-q5wkt 1/1 Running 0 11m
knative-serving webhook-65f8998845-m2z68 1/1 Running 0 11m
kpack kpack-controller-7b8f4744d5-qbrwm 1/1 Running 0 12m
kpack kpack-webhook-bdcb8dfdd-gkv9p 1/1 Running 0 12m
metadata-store metadata-store-app-6969d75d48-fm6k9 2/2 Running 0 11m
metadata-store metadata-store-db-0 1/1 Running 0 67s
metallb-system controller-5fd797fbf7-27w6t 1/1 Running 4 (146m ago) 3h43m
metallb-system speaker-9f5jz 1/1 Running 4 (146m ago) 3h43m
scan-link-system scan-link-controller-manager-86d4cccb6f-qwm8j 2/2 Running 0 13m
secretgen-controller secretgen-controller-6b6bf7bb4-ngln4 1/1 Running 0 92m
service-bindings manager-5b96494bbb-4k7p5 1/1 Running 0 12m
services-toolkit resource-claims-apiserver-77fbfb557b-jtgnl 1/1 Running 0 12m
services-toolkit services-toolkit-controller-manager-7c8dbcbc4c-7bvmt 1/1 Running 0 12m
source-system source-controller-manager-86c85f86d8-kzvt9 1/1 Running 0 12m
spring-boot-convention spring-boot-webhook-78b667b84b-k6d6b 1/1 Running 0 11m
stacks-operator-system controller-manager-fdd95c5cf-9x48t 1/1 Running 0 12m
tanzu-system-ingress contour-cb9f65866-skcdz 1/1 Running 0 12m
tanzu-system-ingress envoy-w4vzd 2/2 Running 0 12m
tap-gui server-6f76d665bd-q4f8v 1/1 Running 0 11m
tap-namespace-provisioning controller-manager-858bf5774d-7ccft 1/1 Running 0 12m
tap-telemetry tap-telemetry-informer-665875499-c2z64 1/1 Running 0 13m
tekton-pipelines-resolvers tekton-pipelines-remote-resolvers-7c488ccc6c-4xmk8 1/1 Running 0 12m
tekton-pipelines tekton-pipelines-controller-76d65c8598-q47jj 1/1 Running 0 12m
tekton-pipelines tekton-pipelines-webhook-d997857cb-858js 1/1 Running 0 12m
```
`tap-values.yaml`に指定したLoadBalancer IPがEnvoyにアサインされていることを確認します。
```
$ kubectl get svc -n tanzu-system-ingress envoy
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
envoy LoadBalancer 10.96.201.188 172.19.255.200 80:31403/TCP,443:31602/TCP 12m
```
インストールされたBuilder一覧を確認します。
```
$ kubectl get clusterbuilder
NAME LATESTIMAGE READY
base harbor.172-19-255-210.sslip.io/tanzu-application-platform/buildservice:clusterbuilder-base@sha256:6bebd5b815488484d2881568869b9e262bfe9512d8343323149625177782d3a9 True
base-jammy harbor.172-19-255-210.sslip.io/tanzu-application-platform/buildservice:clusterbuilder-base-jammy@sha256:109d61c4afc687f464c9c84a8342395c8a9bedec898c0c7a1e88f50021a94b7f True
default harbor.172-19-255-210.sslip.io/tanzu-application-platform/buildservice:clusterbuilder-default@sha256:109d61c4afc687f464c9c84a8342395c8a9bedec898c0c7a1e88f50021a94b7f True
full harbor.172-19-255-210.sslip.io/tanzu-application-platform/buildservice:clusterbuilder-full@sha256:f7ecd1d9298967dd98db51ac3745e22cf8b8a5a1043e8b0e4ac83202b9ceba1b True
full-jammy harbor.172-19-255-210.sslip.io/tanzu-application-platform/buildservice:clusterbuilder-full-jammy@sha256:575cb0da8b74e966e8e115655a37cacf2e3d17605c3fdebea7d5b5cb1c7608cf True
tiny harbor.172-19-255-210.sslip.io/tanzu-application-platform/buildservice:clusterbuilder-tiny@sha256:1b76b0d7a2effd2eba15171df8e4c018936f3f7290a8b2880908abe58c19ffce True
tiny-jammy harbor.172-19-255-210.sslip.io/tanzu-application-platform/buildservice:clusterbuilder-tiny-jammy@sha256:916c6a0111a55e2cd9603dc95818e91ad24b73f785d5e93428adbf1b1872f6f6 True
```
公開されているエンドポイント一覧を確認します。
```
$ kubectl get httpproxy -A
NAMESPACE NAME FQDN TLS SECRET STATUS STATUS DESCRIPTION
metadata-store metadata-store-ingress metadata-store.tap.172-19-255-200.sslip.io ingress-cert valid Valid HTTPProxy
tap-gui tap-gui tap-gui.tap.172-19-255-200.sslip.io tap-gui-cert valid Valid HTTPProxy
```
https://tap-gui.tap.172-19-255-200.sslip.io でTAP GUIにアクセスします。
 ### Workloadのデプロイ
registry-credentialsを作成します。
```
tanzu secret registry add registry-credentials \
--username $(cat robots/tanzu-application-platform-rw.json | jq -r .name) \
--password $(cat robots/tanzu-application-platform-rw.json | jq -r .secret) \
--server harbor.172-19-255-210.sslip.io \
--export-to-all-namespaces \
--yes \
--namespace tap-install
```
Namespaceを作成します。
```
kubectl create ns demo
kubectl label namespaces demo apps.tanzu.vmware.com/tap-ns=""
```
`source-test-scan-to-url` Supply Chainが利用可能になっていることを確認します。
```
$ tanzu apps cluster-supply-chain list
NAME READY AGE
scanning-image-scan-to-url Ready 20s
source-test-scan-to-url Ready 20s
To view details: "tanzu apps cluster-supply-chain get "
```
Tektonパイプラインを作成します。ここではダミーのパイプラインを使用します。
```yaml
cat <<'EOF' | kubectl apply -f - -n demo
apiVersion: tekton.dev/v1beta1
kind: Pipeline
metadata:
name: skip-test-pipeline
labels:
apps.tanzu.vmware.com/pipeline: test
apps.tanzu.vmware.com/language: skip
spec:
params:
- name: source-url
- name: source-revision
tasks:
- name: test
params:
- name: source-url
value: $(params.source-url)
- name: source-revision
value: $(params.source-revision)
taskSpec:
params:
- name: source-url
- name: source-revision
steps:
- name: test
image: alpine
script: |-
echo 'skip'
EOF
```
ScanPolicyを作成します。ここでは`UnknownSeverity`以外は許可するScanPolicyにします。
```yaml
cat <<'EOF' | kubectl apply -f - -n demo
apiVersion: scanning.apps.tanzu.vmware.com/v1beta1
kind: ScanPolicy
metadata:
labels:
app.kubernetes.io/part-of: enable-in-gui
name: scan-policy
spec:
regoFile: |
package main
# Accepted Values: "Critical", "High", "Medium", "Low", "Negligible", "UnknownSeverity"
notAllowedSeverities := ["UnknownSeverity"]
ignoreCves := []
contains(array, elem) = true {
array[_] = elem
} else = false { true }
isSafe(match) {
severities := { e | e := match.ratings.rating.severity } | { e | e := match.ratings.rating[_].severity }
some i
fails := contains(notAllowedSeverities, severities[i])
not fails
}
isSafe(match) {
ignore := contains(ignoreCves, match.id)
ignore
}
deny[msg] {
comps := { e | e := input.bom.components.component } | { e | e := input.bom.components.component[_] }
some i
comp := comps[i]
vulns := { e | e := comp.vulnerabilities.vulnerability } | { e | e := comp.vulnerabilities.vulnerability[_] }
some j
vuln := vulns[j]
ratings := { e | e := vuln.ratings.rating.severity } | { e | e := vuln.ratings.rating[_].severity }
not isSafe(vuln)
msg = sprintf("CVE %s %s %s", [comp.name, vuln.id, ratings])
}
EOF
```
Workloadを作成します。
```
tanzu apps workload apply hello-nodejs \
--app hello-nodejs \
--git-repo https://github.com/making/hello-nodejs \
--git-branch master \
--type web \
--label apps.tanzu.vmware.com/has-tests=true \
-n demo \
-y
```
しばらくして、Workloadの状態を確認すると次の出力のようになります。
```
$ tanzu apps workload get hello-nodejs --namespace demo
📡 Overview
name: hello-nodejs
type: web
namespace: demo
💾 Source
type: git
url: https://github.com/making/hello-nodejs
branch: master
📦 Supply Chain
name: source-test-scan-to-url
NAME READY HEALTHY UPDATED RESOURCE
source-provider True True 4m14s gitrepositories.source.toolkit.fluxcd.io/hello-nodejs
source-tester True True 3m56s runnables.carto.run/hello-nodejs
source-scanner True True 3m40s sourcescans.scanning.apps.tanzu.vmware.com/hello-nodejs
image-provider True True 3m13s images.kpack.io/hello-nodejs
image-scanner True True 2m50s imagescans.scanning.apps.tanzu.vmware.com/hello-nodejs
config-provider True True 2m44s podintents.conventions.carto.run/hello-nodejs
app-config True True 2m44s configmaps/hello-nodejs
service-bindings True True 2m44s configmaps/hello-nodejs-with-claims
api-descriptors True True 2m44s configmaps/hello-nodejs-with-api-descriptors
config-writer True True 2m38s runnables.carto.run/hello-nodejs-config-writer
🚚 Delivery
name: delivery-basic
NAME READY HEALTHY UPDATED RESOURCE
source-provider True True 2m14s imagerepositories.source.apps.tanzu.vmware.com/hello-nodejs-delivery
deployer True True 2m8s apps.kappctrl.k14s.io/hello-nodejs
💬 Messages
No messages found.
🛶 Pods
NAME READY STATUS RESTARTS AGE
hello-nodejs-82ppr-test-pod 0/1 Completed 0 4m11s
hello-nodejs-build-1-build-pod 0/1 Completed 0 3m40s
hello-nodejs-config-writer-bxgxw-pod 0/1 Completed 0 2m44s
scan-hello-nodejs-c79cv-pod 0/7 Completed 1 3m12s
scan-hello-nodejs-mn6pw-pod 0/9 Completed 1 3m59s
🚢 Knative Services
NAME READY URL
hello-nodejs Ready https://hello-nodejs.demo.tap.172-19-255-200.sslip.io
To see logs: "tanzu apps workload tail hello-nodejs --namespace demo --timestamp --since 1h"
```
アプリにアクセスします。
```
$ curl -k https://hello-nodejs.demo.tap.172-19-255-200.sslip.io/
Hello World!!
```
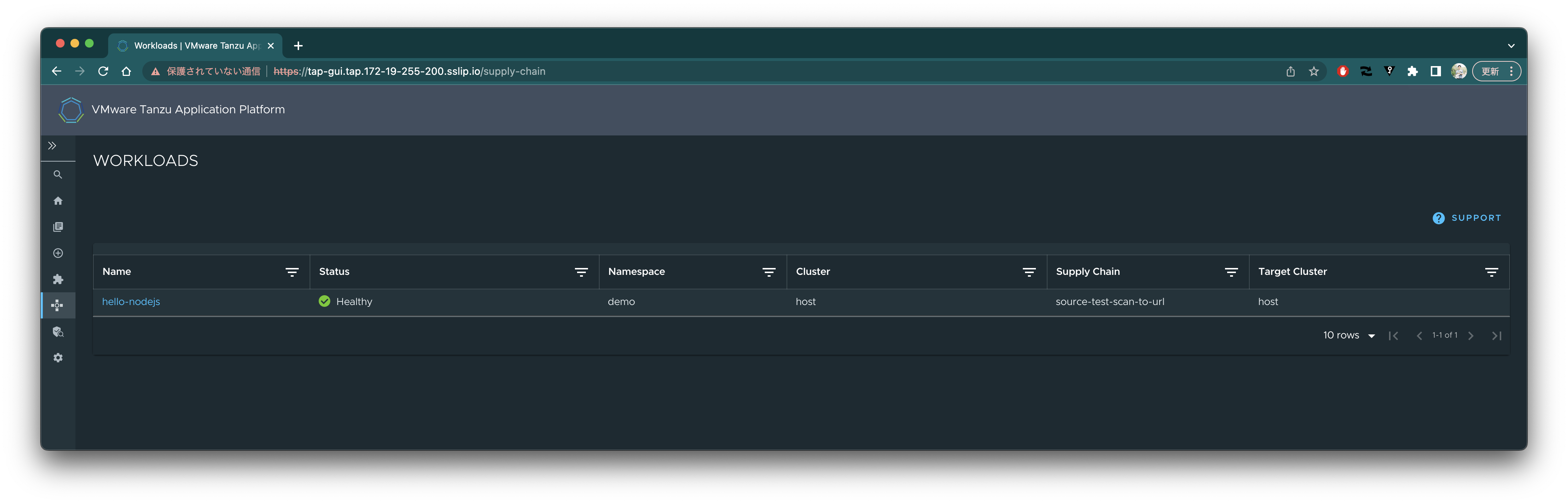
TAP GUIのSupply Chain一覧を確認します。
https://tap-gui.tap.172-19-255-200.sslip.io/supply-chain
### Workloadのデプロイ
registry-credentialsを作成します。
```
tanzu secret registry add registry-credentials \
--username $(cat robots/tanzu-application-platform-rw.json | jq -r .name) \
--password $(cat robots/tanzu-application-platform-rw.json | jq -r .secret) \
--server harbor.172-19-255-210.sslip.io \
--export-to-all-namespaces \
--yes \
--namespace tap-install
```
Namespaceを作成します。
```
kubectl create ns demo
kubectl label namespaces demo apps.tanzu.vmware.com/tap-ns=""
```
`source-test-scan-to-url` Supply Chainが利用可能になっていることを確認します。
```
$ tanzu apps cluster-supply-chain list
NAME READY AGE
scanning-image-scan-to-url Ready 20s
source-test-scan-to-url Ready 20s
To view details: "tanzu apps cluster-supply-chain get "
```
Tektonパイプラインを作成します。ここではダミーのパイプラインを使用します。
```yaml
cat <<'EOF' | kubectl apply -f - -n demo
apiVersion: tekton.dev/v1beta1
kind: Pipeline
metadata:
name: skip-test-pipeline
labels:
apps.tanzu.vmware.com/pipeline: test
apps.tanzu.vmware.com/language: skip
spec:
params:
- name: source-url
- name: source-revision
tasks:
- name: test
params:
- name: source-url
value: $(params.source-url)
- name: source-revision
value: $(params.source-revision)
taskSpec:
params:
- name: source-url
- name: source-revision
steps:
- name: test
image: alpine
script: |-
echo 'skip'
EOF
```
ScanPolicyを作成します。ここでは`UnknownSeverity`以外は許可するScanPolicyにします。
```yaml
cat <<'EOF' | kubectl apply -f - -n demo
apiVersion: scanning.apps.tanzu.vmware.com/v1beta1
kind: ScanPolicy
metadata:
labels:
app.kubernetes.io/part-of: enable-in-gui
name: scan-policy
spec:
regoFile: |
package main
# Accepted Values: "Critical", "High", "Medium", "Low", "Negligible", "UnknownSeverity"
notAllowedSeverities := ["UnknownSeverity"]
ignoreCves := []
contains(array, elem) = true {
array[_] = elem
} else = false { true }
isSafe(match) {
severities := { e | e := match.ratings.rating.severity } | { e | e := match.ratings.rating[_].severity }
some i
fails := contains(notAllowedSeverities, severities[i])
not fails
}
isSafe(match) {
ignore := contains(ignoreCves, match.id)
ignore
}
deny[msg] {
comps := { e | e := input.bom.components.component } | { e | e := input.bom.components.component[_] }
some i
comp := comps[i]
vulns := { e | e := comp.vulnerabilities.vulnerability } | { e | e := comp.vulnerabilities.vulnerability[_] }
some j
vuln := vulns[j]
ratings := { e | e := vuln.ratings.rating.severity } | { e | e := vuln.ratings.rating[_].severity }
not isSafe(vuln)
msg = sprintf("CVE %s %s %s", [comp.name, vuln.id, ratings])
}
EOF
```
Workloadを作成します。
```
tanzu apps workload apply hello-nodejs \
--app hello-nodejs \
--git-repo https://github.com/making/hello-nodejs \
--git-branch master \
--type web \
--label apps.tanzu.vmware.com/has-tests=true \
-n demo \
-y
```
しばらくして、Workloadの状態を確認すると次の出力のようになります。
```
$ tanzu apps workload get hello-nodejs --namespace demo
📡 Overview
name: hello-nodejs
type: web
namespace: demo
💾 Source
type: git
url: https://github.com/making/hello-nodejs
branch: master
📦 Supply Chain
name: source-test-scan-to-url
NAME READY HEALTHY UPDATED RESOURCE
source-provider True True 4m14s gitrepositories.source.toolkit.fluxcd.io/hello-nodejs
source-tester True True 3m56s runnables.carto.run/hello-nodejs
source-scanner True True 3m40s sourcescans.scanning.apps.tanzu.vmware.com/hello-nodejs
image-provider True True 3m13s images.kpack.io/hello-nodejs
image-scanner True True 2m50s imagescans.scanning.apps.tanzu.vmware.com/hello-nodejs
config-provider True True 2m44s podintents.conventions.carto.run/hello-nodejs
app-config True True 2m44s configmaps/hello-nodejs
service-bindings True True 2m44s configmaps/hello-nodejs-with-claims
api-descriptors True True 2m44s configmaps/hello-nodejs-with-api-descriptors
config-writer True True 2m38s runnables.carto.run/hello-nodejs-config-writer
🚚 Delivery
name: delivery-basic
NAME READY HEALTHY UPDATED RESOURCE
source-provider True True 2m14s imagerepositories.source.apps.tanzu.vmware.com/hello-nodejs-delivery
deployer True True 2m8s apps.kappctrl.k14s.io/hello-nodejs
💬 Messages
No messages found.
🛶 Pods
NAME READY STATUS RESTARTS AGE
hello-nodejs-82ppr-test-pod 0/1 Completed 0 4m11s
hello-nodejs-build-1-build-pod 0/1 Completed 0 3m40s
hello-nodejs-config-writer-bxgxw-pod 0/1 Completed 0 2m44s
scan-hello-nodejs-c79cv-pod 0/7 Completed 1 3m12s
scan-hello-nodejs-mn6pw-pod 0/9 Completed 1 3m59s
🚢 Knative Services
NAME READY URL
hello-nodejs Ready https://hello-nodejs.demo.tap.172-19-255-200.sslip.io
To see logs: "tanzu apps workload tail hello-nodejs --namespace demo --timestamp --since 1h"
```
アプリにアクセスします。
```
$ curl -k https://hello-nodejs.demo.tap.172-19-255-200.sslip.io/
Hello World!!
```
TAP GUIのSupply Chain一覧を確認します。
https://tap-gui.tap.172-19-255-200.sslip.io/supply-chain
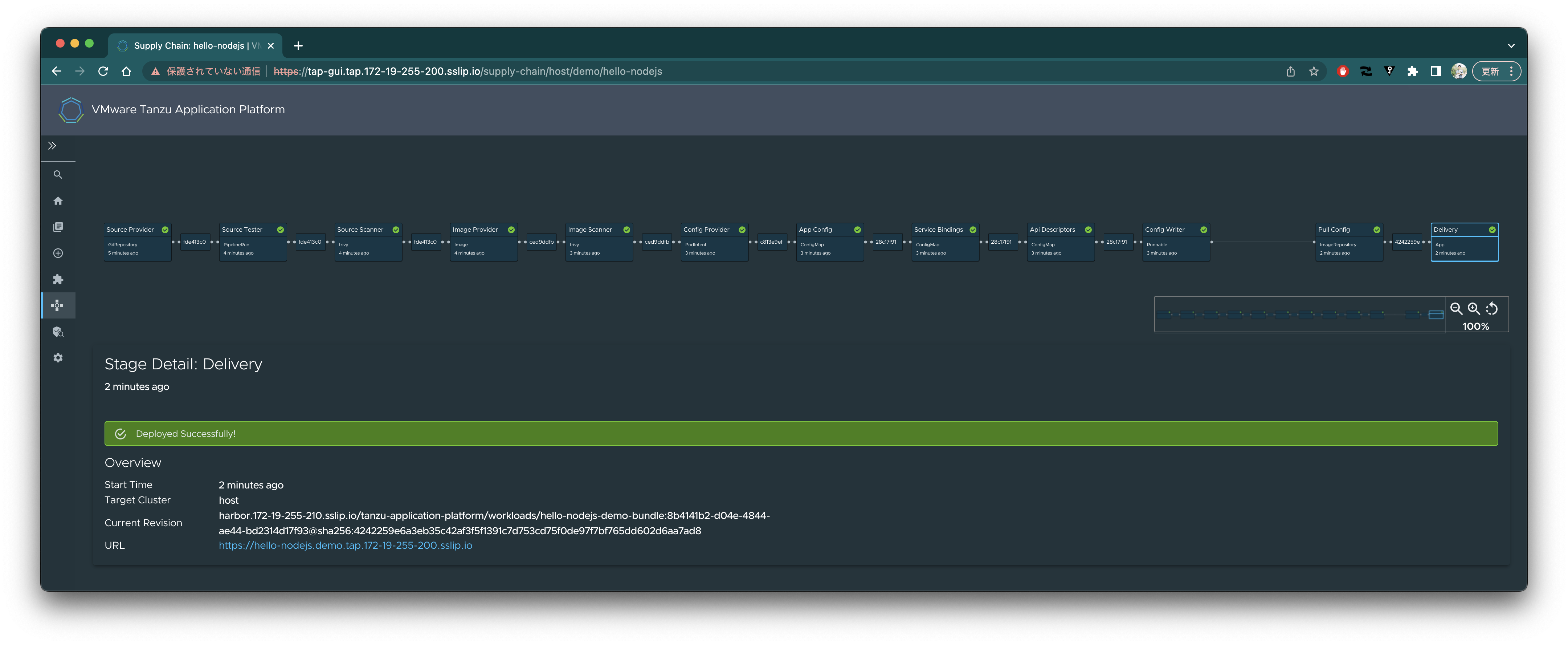
 `hello-nodejs`をクリックします。
https://tap-gui.tap.172-19-255-200.sslip.io/supply-chain/host/demo/hello-nodejs
Workloadが視覚化されています。
`hello-nodejs`をクリックします。
https://tap-gui.tap.172-19-255-200.sslip.io/supply-chain/host/demo/hello-nodejs
Workloadが視覚化されています。
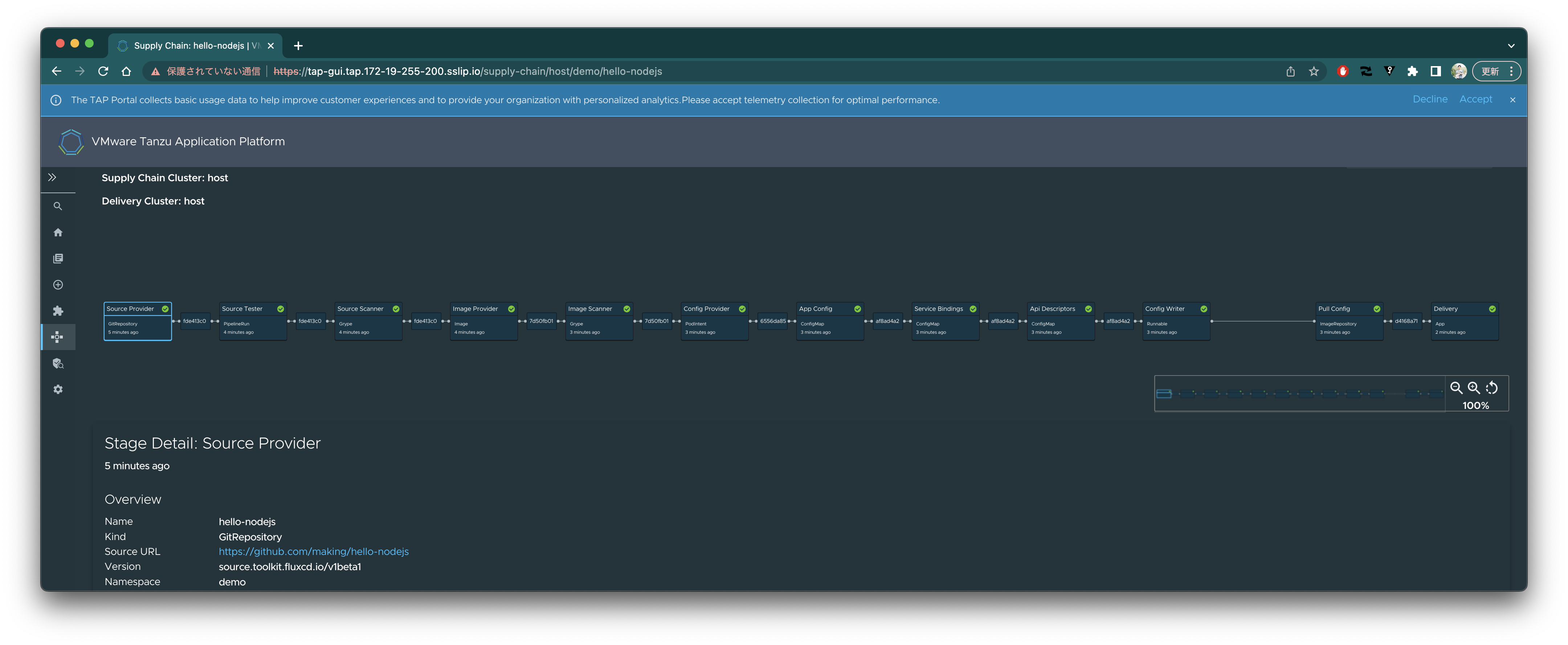 ソースコードの脆弱性一覧を確認できます。(Grypeによるソースコード脆弱性検出は誤検出が多いいです)
ソースコードの脆弱性一覧を確認できます。(Grypeによるソースコード脆弱性検出は誤検出が多いいです)
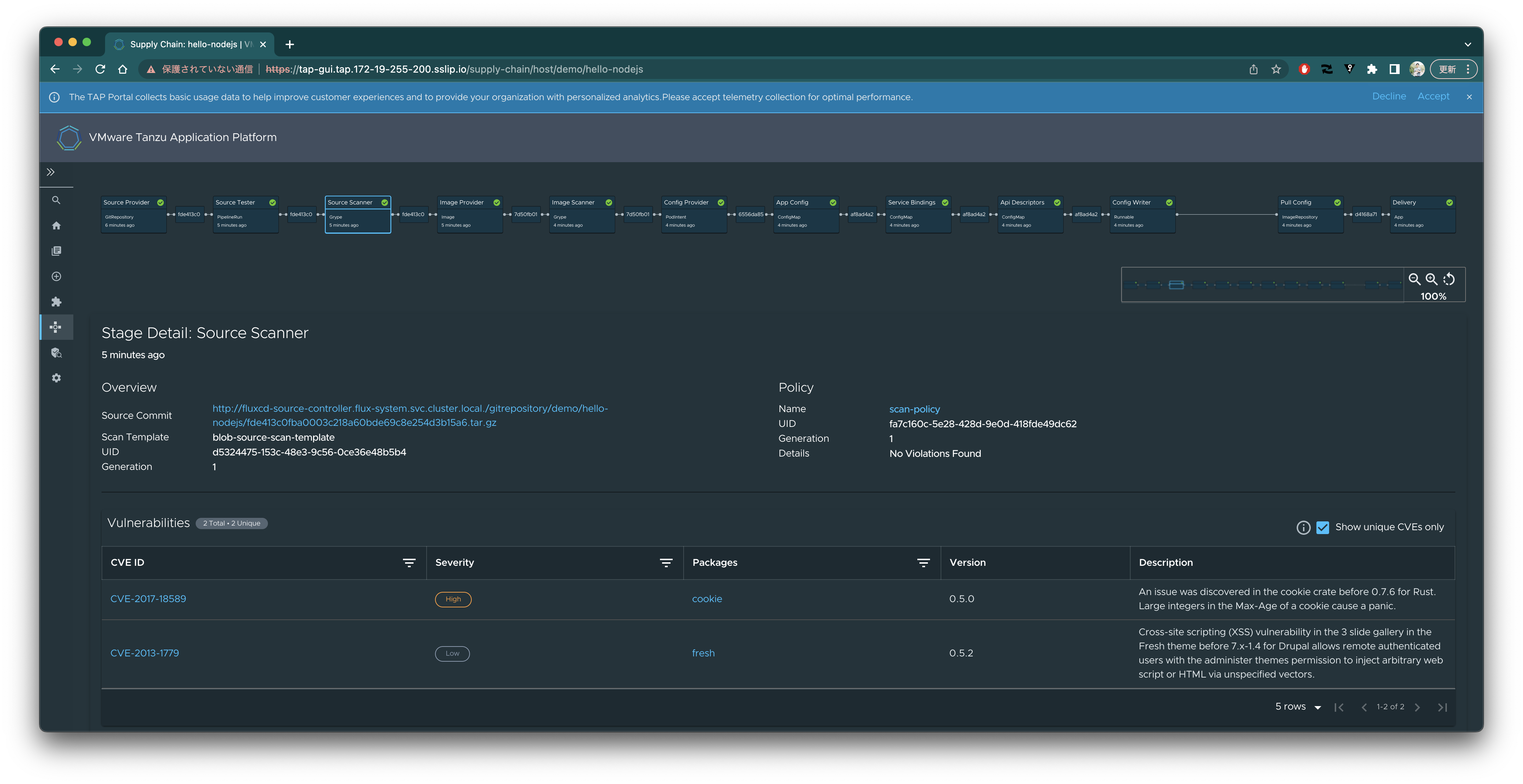 コンテナイメージの脆弱性一覧を確認できます。
コンテナイメージの脆弱性一覧を確認できます。
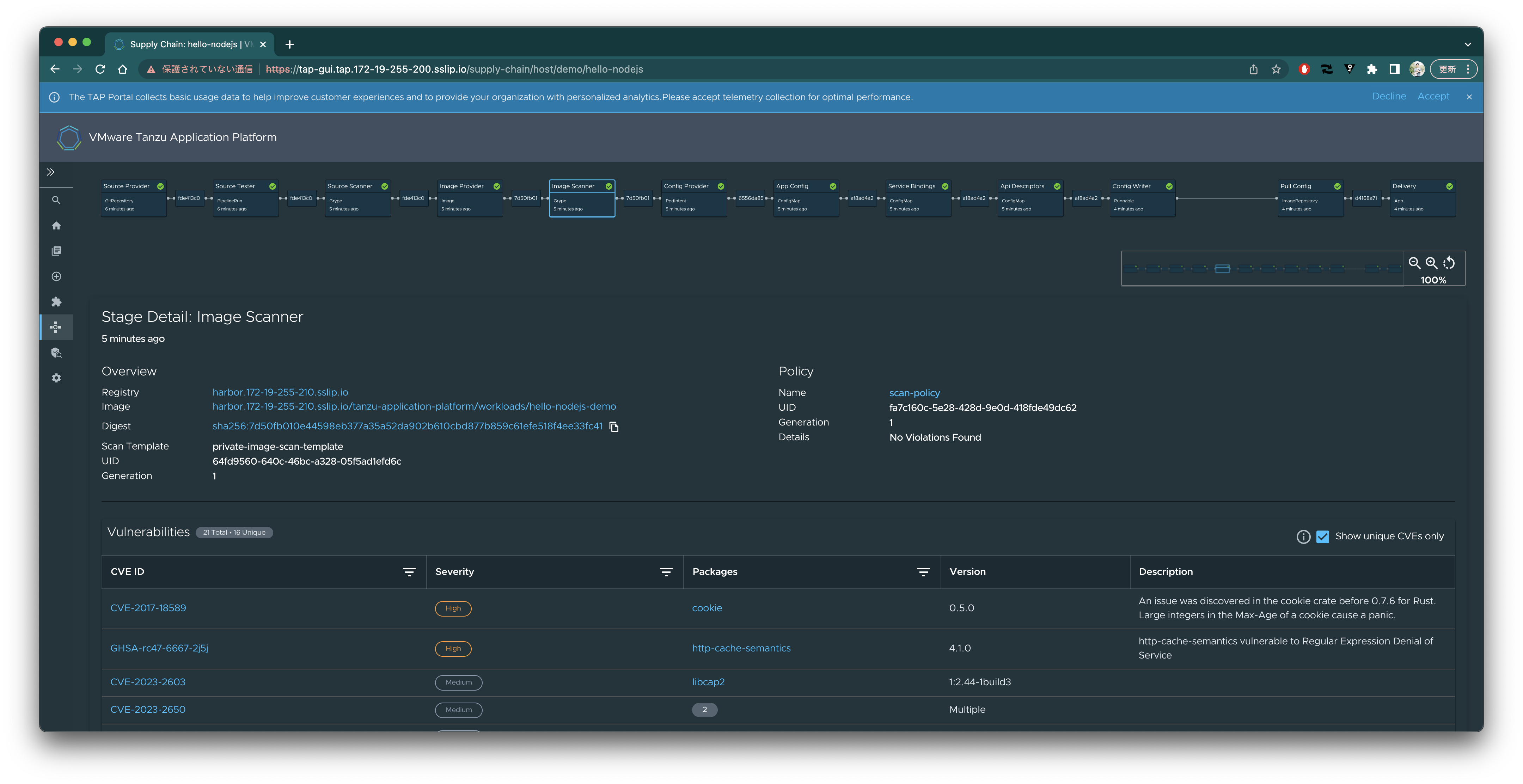 DeliveryをクリックするとアプリのURLが出力されます。
DeliveryをクリックするとアプリのURLが出力されます。